USAF Veteran with a Summa Cum Laude BS in Cyber Operations from DSU, exploring the vast landscape of information technology one day at a time. ἀρετή

Threat Hunting Scenario: TOR
Microsoft Sentinel - Cyber Range Project
August 03, 2025 · 1490 words · 7 min read
Official Cyber Range Project
Threat Hunt Report: Unauthorized TOR Usage
Platforms and Languages Leveraged
- Windows 10 Virtual Machines (Microsoft Azure)
- EDR Platform: Microsoft Defender for Endpoint
- Kusto Query Language (KQL)
- Tor Browser
Table of Contents
Scenario
Management suspects that some employees may be using TOR browsers to bypass network security controls because recent network logs show unusual encrypted traffic patterns and connections to known TOR entry nodes. Additionally, there have been anonymous reports of employees discussing ways to access restricted sites during work hours. The goal is to detect any TOR usage and analyze related security incidents to mitigate potential risks. If any use of TOR is found, notify management.
High-Level TOR-Related IoC Discovery Plan
- Check
DeviceFileEventsfor anytor(.exe)orfirefox(.exe)file events. - Check
DeviceProcessEventsfor any signs of installation or usage. - Check
DeviceNetworkEventsfor any signs of outgoing connections over known TOR ports.
Steps Taken
1. Searched the DeviceFileEvents Table
Searched the DeviceFileEvents table for ANY file that had the string “tor” in it and discovered that the user “chungleboi” downloaded a Tor installer, did something that resulted in many Tor-related files being copied to the desktop, and created a file called tor-shopping-list.txt on the desktop. These events began at: 2025-08-03T14:32:07.4336421Z
Query used to locate events:
DeviceFileEvents
| where DeviceName contains "ortiz"
| where FileName contains "tor"
| order by Timestamp desc
| where InitiatingProcessAccountName == "chungleboi"
| where Timestamp >= datetime(2025-08-03T14:32:07.4336421Z)
| project Timestamp, DeviceName, ActionType, FileName, FolderPath, SHA256, Account = InitiatingProcessAccountName, InitiatingProcessId
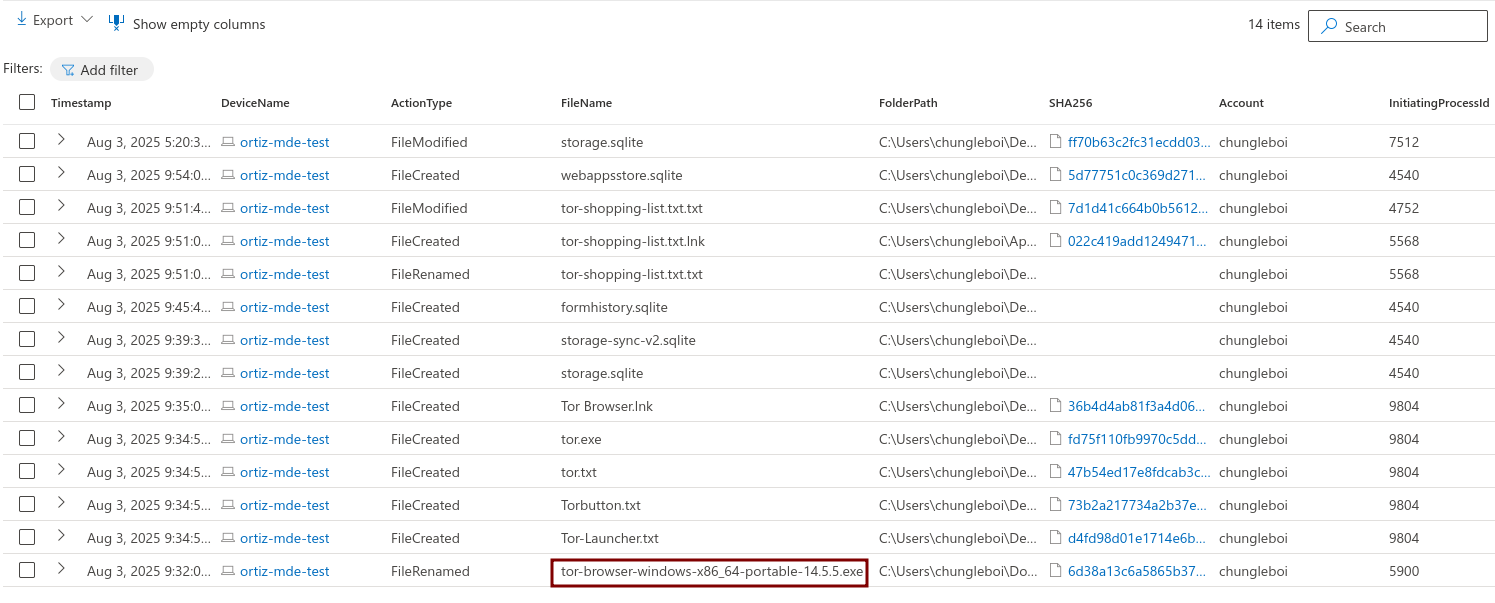
2. Searched the DeviceProcessEvents Table
Searched the DeviceProcessEvents table for any ProcessCommandLine that contained the string tor-browser-windows-x86_64-portable-14.5.5.exe. Based on the logs returned, on August 3rd, 2025, at 9:34:34 AM, a user named “chungleboi” on a computer called “ortiz-mde-test” ran the Tor browser installer from their Downloads folder. The installer was executed with a “/S” flag, which means it ran silently in the background without showing the usual installation prompts or windows to the user.
Query used to locate event:
DeviceProcessEvents
| where DeviceName contains "ortiz"
| where ProcessCommandLine contains "tor-browser-windows-x86_64-portable-14.5.5.exe"
| project Timestamp, AccountName, DeviceName, ActionType, FolderPath, SHA256, ProcessCommandLine
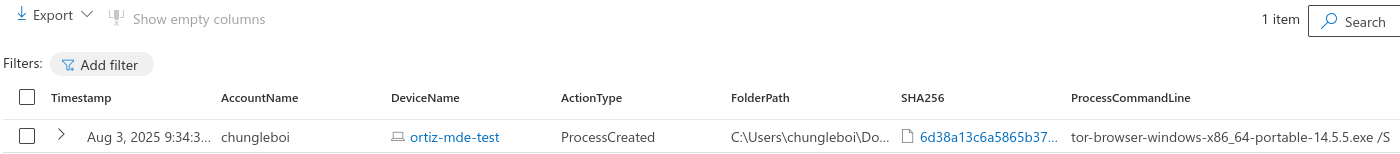
3. Searched the DeviceProcessEvents Table for TOR Browser Execution
Searched the DeviceProcessEvents table for any indication that user “chungleboi” actually opened the Tor browser. There was evidence that they did open it at 2025-08-03T14:39:23.1647585Z. There were several other instances of firefox.exe (Tor) as well as tor.exe spawned afterwards.
Query used to locate events:
DeviceProcessEvents
| where DeviceName contains "ortiz"
| where FileName has_any ("tor.exe", "firefox.exe", "tor-browser.exe")
| project Timestamp, AccountName, DeviceName, ActionType, FolderPath, SHA256, ProcessCommandLine
| order by Timestamp desc
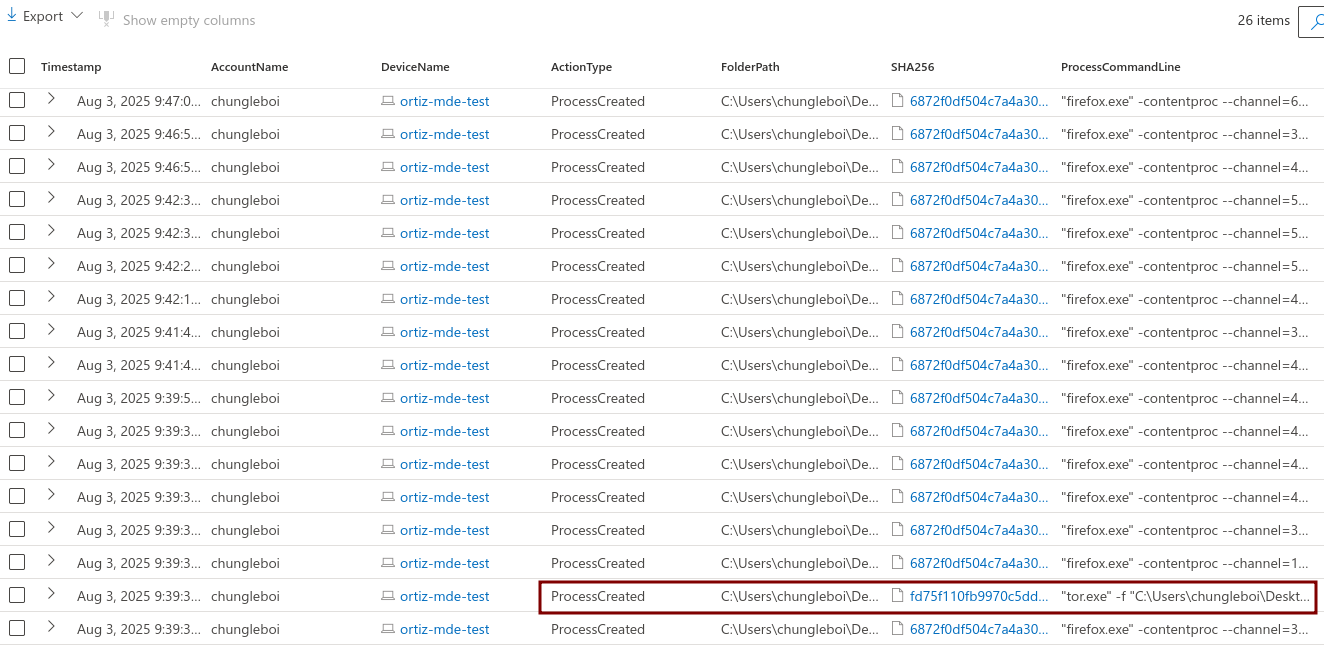
4. Searched the DeviceNetworkEvents Table for TOR Network Connections
Searched the DeviceNetworkEvents table for any indication that the Tor browser was used to establish a connection using any of the known Tor ports. At 2025-08-03T14:39:58.5567161Z, an employee on the “ortiz-mde-test” device successfully established a connection to the remote IP 185.220.101.198 via port 443. The connection was initiated by the process tor.exe, located in the folder c:\users\chungleboi\desktop\tor browser\browser\torbrowser\tor\tor.exe. There were a few more connections made over other ports.
Query used to locate events:
DeviceNetworkEvents
| where DeviceName == "ortiz-mde-test"
| where InitiatingProcessFileName in ("tor.exe", "firefox.exe")
| where RemotePort in ("9001", "9030", "9040", "9050", "9051", "9151", "80", "443")
| project Timestamp, DeviceName, ActionType, RemoteIP, RemotePort, RemoteUrl, InitiatingProcessAccountName, InitiatingProcessFileName, InitiatingProcessId, InitiatingProcessParentId, InitiatingProcessFolderPath
| order by Timestamp desc
| where Timestamp >= datetime(2025-08-03T14:39:25.0575445Z)
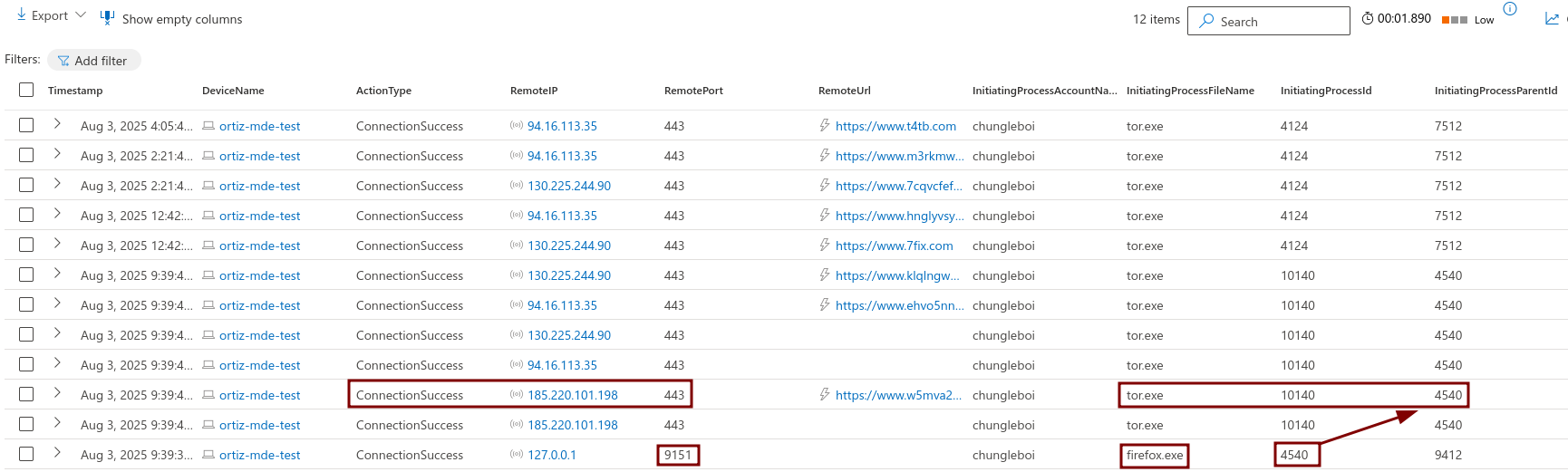
Chronological Event Timeline
Phase 1: Initial Download and Installation (9:32 AM - 9:35 AM)
9:32:07 AM - Initial Tor Browser installer file appears
- Event: FileRenamed - tor-browser-windows-x86_64-portable-14.5.5.exe
- Location: C:\Users\chungleboi\Downloads\
- SHA256: 6d38a13c6a5865b373ef1e1ffcd31b3f359abe896571d27fa666ce71c486a40d
9:34:34 AM - Tor installer executed with silent flag
- Event: ProcessCreated - tor-browser-windows-x86_64-portable-14.5.5.exe /S
- Significance: Silent installation (/S flag) suggests an attempt to avoid detection
9:34:54 AM - Tor application files created on desktop
- Multiple Tor-related files created, including:
tor.exe(main Tor executable)- License files (tor.txt, Torbutton.txt, Tor-Launcher.txt)
9:35:04 AM - Desktop shortcut created
- Event: FileCreated - Tor Browser.lnk
- Location: C:\Users\chungleboi\Desktop\Tor Browser\
Phase 2: First Tor Browser Session (9:39 AM - 9:54 AM)
9:39:23 AM - Tor browser launched
- Event: ProcessCreated - firefox.exe (multiple instances)
- Significance: First evidence of a user actively opening the Tor browser
9:39:26 AM - Browser profile initialization
- Event: FileCreated - storage.sqlite
- Location: Profile directory indicating browser setup
9:39:27-33 AM - Multiple Firefox content processes spawned
- Multiple child processes created for tabs, GPU, and utility functions
- Indicates active browser usage with multiple tabs/processes
9:39:31 AM - Tor daemon process started
- Event: ProcessCreated - tor.exe with full configuration
- Configuration: Local SOCKS proxy on 127.0.0.1:9150, Control port 9151
- Significance: Tor network daemon is now active and ready for connections
9:39:33 AM - First internal connection established
- Event: ConnectionSuccess to 127.0.0.1:9151
- Process: firefox.exe
- Significance: Browser connecting to local Tor control port
9:39:40 AM - First external Tor connections established
- Connections to: 185.220.101.198:443 (www.w5mva25htg5.com)
- Process: tor.exe (PID: 10140)
- Significance: First evidence of actual Tor network usage
9:39:44-45 AM - Additional Tor relay connections
- Significance: Building a Tor circuit through multiple relays
- Connections to:
- 130.225.244.90:443 (www.klqlngww7.com)
- 94.16.113.35:443 (www.ehvo5nnbfa.com)
9:39:59 AM - 9:47:54 AM - Continued browser activity
- Multiple additional Firefox content processes created
- Indicates sustained browsing activity with multiple tabs
9:45:45 AM - Form history database created
- Event: FileCreated - formhistory.sqlite
- Significance: Indicates the user potentially filling out forms or searches
9:51:07 AM - Suspicious file created
- Event: FileCreated/FileRenamed - tor-shopping-list.txt
- Location: C:\Users\chungleboi\Desktop\
- Significance: User created a file with “tor” and “shopping” in the name - potentially suspicious
9:51:45 AM - Shopping list file modified
- Event: FileModified - tor-shopping-list.txt.txt
- SHA256: 7d1d41c664b0b56129bf2e1cfa45a36e214ceef37ad4a3446d7f62ab11f005ff
- Significance: User actively editing the suspicious file
9:54:03 AM - Web applications storage created
- Event: FileCreated - webappsstore.sqlite
- Significance: End of first active session
Phase 3: Second Tor Browser Session (12:41 PM - 2:21 PM)
12:41:51 PM - Second Tor session initiated
- Event: ProcessCreated - firefox.exe (multiple instances)
- Significance: User returning to the Tor browser hours later
12:41:57 PM - Tor daemon restarted
- Event: ProcessCreated - tor.exe with the same configuration
- Process ID: Different PID (4124) indicating a fresh start
- Parent Process: 7512 (different from first session)
12:42:43 PM - New Tor connections established
- Significance: Accessing different onion sites in the second session
- Process: tor.exe (PID: 4124)
- Connections to:
- 94.16.113.35:443 (www.hnglyvsychy4vtvg6c3g.com)
- 130.225.244.90:443 (www.7fix.com)
2:21:45-46 PM - Final network activity
- Significance: Last recorded Tor network activity
- Connection to:
- 130.225.244.90:443 (www.7cqvcfefqw5kxwd.com)
- 94.16.113.35:443 (www.m3rkmwg3lotidtgdb7.com)
Summary and Risk Assessment
Timeline Summary
- 9:32 AM: Tor installer downloaded to the system
- 9:34 AM: Silent installation executed to avoid detection
- 9:39 AM: First active Tor browsing session begins
- 9:51 AM: Suspicious “tor-shopping-list.txt” file created and modified
- 12:41 PM: Second Tor browsing session initiated
- 2:21 PM: Final network activity recorded
Key Findings
- Duration: Approximately 5 hours of Tor-related activity
- Sessions: Two distinct usage sessions indicating deliberate, repeated use
- Network Activity: Multiple connections to onion services, suggesting active dark web browsing
- Suspicious Content: Creation of “tor-shopping-list.txt” file raises concerns about potential illicit marketplace activity
- Evasion Techniques: Use of the silent installation flag “/S” suggests awareness of security monitoring
Risk Level: HIGH
The evidence indicates intentional installation and sustained use of the Tor browser for accessing onion services, combined with the creation of a suspicious “shopping list” file that may indicate illicit marketplace activity. The user demonstrated security awareness by using silent installation, suggesting potential malicious intent rather than legitimate privacy usage.
Recommended Actions:
- Investigate the contents of the
"tor-shopping-list.txt"file - Review user “chungleboi” for policy violations
- Implement network monitoring for Tor traffic
- Consider blocking Tor browser installation on managed devices
- Conduct a user interview regarding the business justification for Tor usage
Response Taken
TOR usage was confirmed on endpoint ortiz-mde-test by the user chungleboi. The device was isolated, and the user’s direct manager was notified.






